Data breaches exposed a staggering 6 million records in the first quarter of 2023, underscoring the critical importance of secure information transfer. Whether you're exchanging data internally or with external parties, utilizing a secure method to share information is paramount to safeguarding it from compromise.
In this article, we'll delve into the world of Secure File Transfer Protocol (SFTP), exploring how to access an SFTP server securely and everything you need to know to make it work seamlessly.
SFTP vs. FTP What’s the Difference?
You may often hear the terms SFTP and FTP used interchangeably, but they are distinct in their methodologies, despite sharing the same purpose of transferring files between computers on a network.
FTP
File Transfer Protocol (FTP) is a widely-used method for transferring files in batches between computers. However, it lacks the security measures necessary to protect sensitive information.
SFTP
Secure File Transfer Protocol (SFTP) serves as a more secure alternative to FTP. The difference between the two is that SFTP adds a layer of security. It enhances security by encrypting data before file sharing, providing a higher level of protection compared to standard FTP. Additionally, SFTP employs authentication through user IDs, passwords, and, for advanced security, SSH keys.
Why Is It Important?
The significance of secure file sharing cannot be overstated, especially for organizations required to comply with strict security standards like HIPAA, CCPA, GDPR, SOC2, and SOX. Remaining compliant with these standards is a challenging endeavor, but with Integrate.io's ETL tool integrated with SFTP, you can keep private information secure and avoid severe penalties.
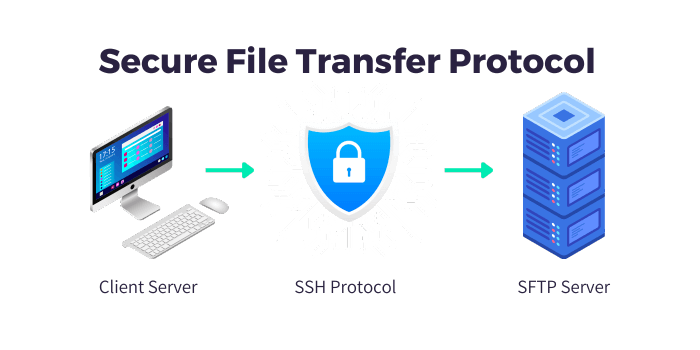
How Does Secure File Transfer Protocol Work?
Transferring files between computers is an in-depth process that involves several steps:
1) Request to Establish Connection
- The requesting computer (client) contacts the server to request to establish a connection. The request uses port 22 on the firewall at the server’s site.
- A listener on the server monitors for incoming connection requests.
2) Negotiate Security Parameters
- Both parties must negotiate pre-defined security parameters to establish a connection.
- The negotiation involves both parties choosing a specific encryption method to be used for the connection.
- Once the connection encryption method is determined, both parties negotiate what protocol will be used to transfer data.
3) Authentication
- The client sends login credentials to the server.
- The client may also be required to authenticate using a key/value pair.
- If a key is required, a set of public and private keys are generated. The public key resides at the server while the private key resides with the client.
- The client will provide the public key during the authentication process.
- If the keys on the client and server match, the server grants access.
Integrate.io provides full support for connecting to an SFTP server, using industry-standard encryption methods to ensure the privacy of your data during transfer.
Connecting to a Secure File Transfer Protocol Server
Before accessing an SFTP server, you'll need a client application and the server's details. Here's a step-by-step process to get started:
1) Determine the Authentication Method
The first step in the process is to determine the authentication method. During this process, you establish a password required for authentication. You can configure public and private keys to use for authentication as well if required. To take security measures even further, you can optionally set a passphrase that would be required to establish a connection.
2) Configure the Server
The sender stores files for client requests. The server uses the SSH protocol for transmission. You will also set up the directory where files are stored, and create the necessary groups and user logins to establish a connection.
3) Configure the Firewall
After configuring the server, you need to configure the firewall to allow connections. This step involves setting a one-port SSH tunnel on port 22.
4) Configure Client
The last step is to configure a client at the requesting computer. The administrator on the client-side of the connection completes these steps. The client’s administrator installs an SFTP client and configures the following:
- Host name of the SFTP server
- The security protocol in use
- User name to be used for the connection
- Password to use for the connection
- The private key for the user
Integrate.io allows you to transfer files securely between vendors, or other third parties using SFTP. The tool can access any port configured for SFTP to facilitate the transmission.
Moving Beyond SFTP With APIs
While SFTP serves as an excellent solution for batch file transfers, real-time data requirements may demand a more agile approach. Many organizations choose to graduate to Application Programming Interfaces (APIs) for secure and on-demand information sharing between systems. Integrate.io offers hundreds of pre-built connections to APIs like Salesforce, simplifying the integration of data securely and reliably.
Connecting to an SFTP Server using Integrate.io
Sharing information between computers gives companies a holistic view of real-time data for informed decision-making. The value in that data can only be realized if the information is accurate. Sharing files over SFTP ensures a private connection for transmitting the information. Integrate.io features a robust set of integrations that allow you to access data files on any SFTP server. For more details on SFTP, how to access an SFTP server, how to make the switch to APIs, or any other data integration needs, schedule a demo to see how Integrate.io can help.