"At this point, cloud adoption is mainstream," says Research Vice President at Gartner Sid Nag.
The momentum for cloud adoption continues to rise, and many companies find themselves in a Catch 22 scenario. The fear of storing sensitive data in a public cloud is intense and leaping to dissolve on-premise setups that have been around for years, if not decades, is unsettling. However, the upsides outweigh the negatives, and at this stage, they can't afford not to leverage new-age applications and advanced analytics available in the cloud.
Utilizing cloud solutions generally includes plans to reduce costs, consolidate billing, ensure server availability, and plan for disaster recovery. The cloud offers a host of benefits over self-owned IT such as cost savings, faster deployments, better performance, scalability, flexibility, and even shifting budgets from capital expenditures to operational expenditures. According to Gartner Group, the worldwide public cloud services market is forecast to grow 17% in 2020 to total $266.4 billion, up from $227.8 billion in 2019.
When and why should you choose to initiate an on-prem to cloud migration for your business? And what reasons, if any, could there be for holding back?
Data Security: On-Premise vs. Cloud
In this section we will discuss the key differences between on-premise security and security available in the cloud.
On-Premise Security
There are three fundamental principles to consider when deciding how to access sensitive data securely, namely: Confidentiality, Integrity, and Availability. These principals are collectively known as the CIA triad.
On-premises servers operate within the traditional enterprise computing paradigm. In this implementation, all hardware and software reside in-house. A business purchases and maintains its hardware and usually houses it in a secure, climate-controlled room onsite, utilizing specialized IT support to manage the equipment. IT professionals must implement necessary procedures such as disaster recovery internally and stay up-to-date with the latest software updates and perform regular backups; the business must buy and install physical hardware parallel with growth; there is no elasticity.
Many companies with sensitive data (i.e., legal, healthcare, and financial) have strict storage policies and can only be compliant with these regulations with an on-premise solution, not to mention the security implications of storing the information in a data center hundreds of miles away. Furthermore, security experts sometimes want tangible hardware to feel safe.
However, on-premise solutions cannot protect against force majeure events such as extreme weather, freak accidents, or elaborate break-ins. Cloud platforms, on the other hand, pour millions into mitigation and consolidation strategies. In this regard, they operate on a different level.
In the modern era, on-premise security generally operates in a completely different paradigm to the cloud. Most on-premise security platforms don't utilize application programming interfaces, and as a result, most on-prem environments have little to no automation. In contrast to public cloud environments, on-prem is almost always IT-driven and security governed. On-premise platforms utilize static resources and perimeter-based security boundaries as opposed to dynamic resources and ephemeral security boundaries.
Cloud Security
Cloud security is generally very robust and safe as each platform has teams of highly trained professionals watching over them and rigid security protocols in place. However, it is essential to look into their default security offerings and upskill employees in basic security hygiene practices. After all, breaches are usually due to human error. According to Gartner, 95% of cloud-based security failures through 2020 will be the customers' fault; for instance, if they fall for a phishing scheme, careless configuration, or easy-to-crack passwords.
Additionally, if a company operates with sensitive data, a deeper dive into the cloud provider's security protocols is recommended. For example, healthcare companies should comply with the Health Insurance Portability and Accountability Act (HIPAA), and educational institutions with the Family Educational Rights and Privacy Act (FERPA). Companies using credit card payments have to follow the Payment Card Industry Data Security Standard (PCI DSS). Also, secure collaboration tools for document sharing can contribute to improved security.
In general, cloud security does offer several out of the box features that are hugely beneficial to security:
- Automatic patching: Unpatched software is among the leading causes of malware infections worldwide. Malicious attackers often exploit critical exploits only a few hours after their public release.
- DDoS mitigation: DDoS attacks are prevalent for cloud platforms - their teams are well versed in this area. Hence they have implemented multiple strategies to mitigate against this. DDoS defense involves deploying detection systems, implementing barriers, and absorbing attacks by scaling to prevent attackers from overwhelming or disabling access to your services or applications.
- Encryption at rest: for example, Google Cloud Platform encrypts customer data stored at rest by default; the user does not have to encrypt or configure anything themselves. Encryption at rest reduces the surface of attack by effectively "cutting out" the lower layers of the hardware and software stack. Even if these lower layers are compromised (for example, through physical access to devices), those devices' data is not compromised if adequate encryption is in place.
- Encryption in-transit: cloud providers ensure data in transit is always transmitted using strong in-transit encryption standards (SSL/TLS certificates) and through a secure connection. For adequate protection, one must encrypt before transmission; authenticate endpoints, decrypt and verify data on arrival. Is your security up to date with the latest encryption standards? Check out Google’s Encryption in transit whitepaper for a deeper dive.
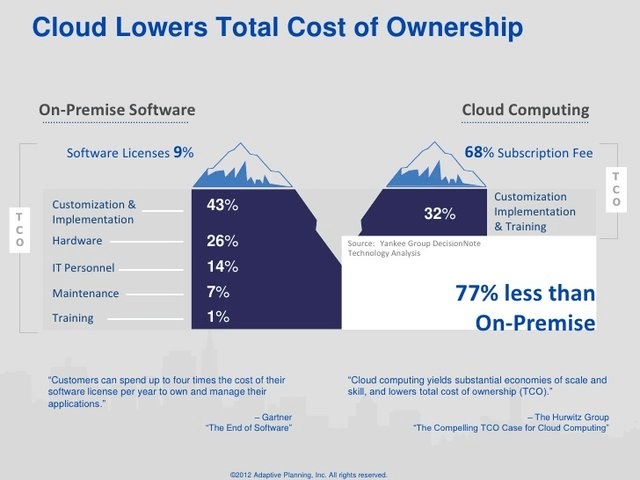
Migration Costs
Finding the actual cost of any significant change to a complex system is highly nuanced and requires weighing many dynamic variables.
Step one is to obtain an objective view of current IT operations. You must divide such costs into two broad categories at the most general level: direct and indirect costs.
The most significant direct cost for an on-premise setup is usually purchasing new gear (servers, switches, etc.). Second and third to that are maintenance and support, including the replacement of hardware, scaling infrastructure on-site, and software updates.
Other examples of direct costs include:
- IT support staff salaries
- Software licenses; support subscriptions
- IT facility costs
- Power and data-connection costs for the IT facility
- Training for both the technical staff and the end-users
Indirect costs are more nuanced and may include the following:
- HR and accounting for managing IT employees
- Cost associated with housing IT staff in a physical location.
You also have several different options regarding what sort of cloud-based infrastructure your company needs. The best option for you depends on your current circumstances and relationship with risk:
- In-house/Private Cloud: Maximizes the legacy investment by retaining everything in-house, but leaves a capital intensive and high-cost structure in place. Most suitable for those applications with strict security or regulatory compliance needs or high migration costs.
- Co-location: Enables faster implementation due to avoiding building a new datacenter. Still, it retains all of the disadvantages of the in-house solution in terms of high-cost and limited ability to respond to demand surges.
- Hybrid Cloud: Retains several advantages of public cloud, primarily cost-effective elastic surge capacity. Hybrid clouds are a compromise between private clouds and public clouds.
- External/Public Cloud: Maximizes the benefits of a low-cost structure and rapid capacity increases, but the legacy on-premise system dissolution.
Related Reading: What is Data Migration?
The calculation resources listed below can help your company calculate potential cloud infrastructure costs.
- AWS (Amazon Web Services) Simple Monthly Calculator
- AWS Total Cost of Ownership (TCO)
- Amazon Elastic Kubernetes Service (EKS)
- Google Cloud Platform Pricing Calculator
- IBM Cloud Cost Estimator
- Rackspace Cloud Pricing Calculator
Cost Benefits of Cloud
Leaping to cloud infrastructure is, of course, a risk, but the long term cost-benefit is ultimately an upside in all respects financially.
- Economies of Scale: Cloud providers purchase and operate computing resources globally, utilizing economies of scale such as,
- Supply-Side Savings: Large-scale data centers (DCs) results in lower costs per server)
- Demand-Side Aggregation: Aggregating demand for computing smooths overall variability. Hence utilization rates increase.
- Multi-Tenancy Efficiency: When migrating to a multi-tenant application model, an increase of tenants lowers the application management and server cost per tenant. As companies utilize the shared resources provided by this architecture, they avoid the substantial up-front CAPEX costs of buying expensive infrastructure - with this pay-as-you-go pricing model, companies pay only for what they use, scaling up or down as needed elastically.
- Global Reach: cloud computing results in substantial savings; as servers no longer need to be housed on-premises—they can be accessed from anywhere in the world— resulting in a dramatic reduction in labor costs. No IT staff required for maintaining, deploying, and troubleshooting hardware on-site.
Cloud Migration Concerns
With all the benefits of working from the cloud, why have some businesses been slow to make the switch?
Primarily because of concerns relating to data loss, compliance, and breaches. Barracuda networks reported that 70% of the business executives surveyed felt security concerns had held back wider public cloud adoption. Across all sectors, Barracuda sees organizations moving their infrastructure to the public cloud, but security is the biggest concern, which is slowing faster adoption. 70% of organizations named security as a critical restriction to its implementation. Further, 38% said that costs also hinder greater public cloud adoption, and 28% named compliance as one of the most massive roadblocks.
Related Reading: Data Security Threats and Compliance
Troy Hunt, an Australian Web Security Expert, shares an interesting perspective in response to these concerns:
“On the one hand, you may hand over physical control, but on the other hand, you’re almost certainly doing so to an organization better-equipped to manage computing environments than your own...Then there are concerns around the increased attack surface of putting services in the cloud, but there are great possibilities with virtualized networks and access to features that were previously cost-prohibitive for many organizations (WAFs, HSMs, etc.). So think of the cloud as ‘different’ and make the most of those hybrid scenarios where you can gradually move assets across in a fashion that suits your own organization’s comfort level."
As Troy pointed out, the hybrid approach has become a popular migration strategy for enterprises. A hybrid cloud is essentially a computing environment that combines public and private clouds by allowing data and applications to distribute and share between them. As computing and processing demand fluctuates, the hybrid approach gives one the ability to automatically scale their on-premises infrastructure up to the public cloud to manage possible overflow—without giving third-party data centers access to their data in the process.
This trend is clear and reflected by IDG, a Research firm that recently published its The State of IT Modernization 2020 study, which states: "64 percent of organizations that have completed their initial IT modernization initiatives have switched from an all-private or all-public cloud strategy to a hybrid cloud approach, again highlighting the trial-and-error that many companies undergo to find the optimal cloud path for their needs."
Cloud Integration with Integrate.io
At Integrate.io, we understand how intimidating it can be to migrate to the cloud. That's why data security and compliance are two of our cloud-based ETL service’s most critical aspects, and why we've incorporated the most advanced data security and encryption technology into our platform, such as:
- Physical infrastructure hosted by accredited Amazon Web Service (AWS) technology
- Advanced preparations to meet the EU General Data Protection Regulation (GDPR) standards
- SSL/TLS encryption on all our websites and microservices
- Field Level Encryption
- Encryption of sensitive data anytime it's “at rest” in the Integrate.io platform using industry-standard encryption
- Constant verification of our security certificates and encryption algorithms
- Operating system access limited to Integrate.io staff and requiring a username and key authentication
- Firewalls that restrict access to systems from external networks and between systems internally
If you'd like to know more about our data security standards and migration tools, contact the Integrate.io team now.